其实这个比较简单了,ida的f5都能清晰地看出来
1 | void __noreturn start() |
我们看看sub_4022E0
1 | char sub_4022E0() |
我们再看sub_402270,这里就比较简单了,就是对第一个字节进行判断,跟着利用2,3个字节对dword_40423C后面的数据进行操作
1 | char __stdcall sub_402270(int a1, int a2, char a3) |
写代码
1 | class VM: |
结果
其实这个比较简单了,ida的f5都能清晰地看出来
1 | void __noreturn start() |
我们看看sub_4022E0
1 | char sub_4022E0() |
我们再看sub_402270,这里就比较简单了,就是对第一个字节进行判断,跟着利用2,3个字节对dword_40423C后面的数据进行操作
1 | char __stdcall sub_402270(int a1, int a2, char a3) |
写代码
1 | class VM: |
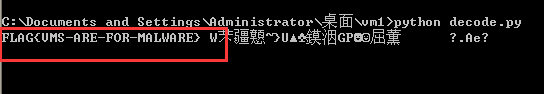
结果


微信支付

支付宝
